Evolution AB's Asian headwinds
$EVO's Asian operations have faced a severe challenge in the form of organized cybercrime. This article explains the nature of the threat, the company’s response, and the long-term implications
Introduction
In my recent deep-dive memo on Evolution AB, I concluded that the company was a very compelling investment opportunity, with an estimated 33% CAGR over the coming five years, thus handsomely beating my hurdle rate of 20%. A core pillar of the investment thesis is the assumption that growth in the crucial Asian market will re-accelerate as the company moves past its recent challenges.
While management has consistently stated that it is "very hard to quantify the Asian growth" impact precisely, the effect is starkly visible in the company's reported financial data. The cyberattacks effectively slammed the brakes on what was previously a key engine of growth for the company, and has pushed the company’s profit margin downwards while trying to re-solve the issues.
While I touched upon the "criminal cyber activity" in the previous report, the complexity and importance of this issue is a key parameter for the entire investment case and deserves its own dedicated analysis. This report is that deep dive. My goal is to go beyond management's commentary and build a clear view of the threat, the company's response, and the long-term implications for investors.
Wishing you a good read!
What does “Criminal Cyber Activity" mean?
Defining the economics of theft
Since first disclosing the issue in late 2024, Evolution’s management has consistently used strong terminology: “cyberattacks,” “theft,” “fraud,” and “criminal cyber activity.” Unlike typical content piracy, this is direct product theft. Criminal operators intercept Evolution’s live casino video feeds, strip out protections, and embed them into their own unlicensed casino front-ends.
By doing so, these groups capture all player losses, the equivalent of the house’s gross gaming revenue, without bearing any of Evolution’s costs for studios, dealers, or licensing. In other words, they free-ride on Evolution’s capital and operations while keeping the entire house edge. Because this generates immediate, recurring cash flows, the incentive for criminals is strong, making the problem more than a nuisance: it is an attack on the integrity of Evolution’s B2B business model.
How criminals steal the streams
Firstly, and important also for understanding the moat, it is clear that Evolution's live casino product is a complex technological offering. The live casino stack integrates multi-camera HD capture, OCR to translate physical gameplay into data, and a table-level Game Control Unit (GCU) that encodes and distributes the stream. The attacks target this distribution chain. Based on industry security analysis and the nature of observed leakage, three sophisticated vectors are most likely:
Vector 1: CDN leeching and DRM bypass: The most probable and effective method. Attackers compromise a downstream licensed operator, reverse-engineer the app, and extract direct stream URLs plus DRM keys. With those credentials, they pull pristine feeds from Evolution’s CDN as if they were authorized traffic, thus evading front-end safeguards and blending in with legitimate requests.
Vector 2: Infrastructure Exploitation: Criminals scan for weak links across Evolution’s and partners’ networks such as misconfigurations, unpatched servers, exposed services. Once inside, they deploy stream-ripping tooling (e.g., ffmpeg) on the compromised host to capture the feed high in the distribution path and relay it to illicit servers. This is a direct network intrusion that enables industrial-scale redistribution.
Vector 3: Advanced Stream Ripping: A lower-tech but viable path. Criminals subscribe through a licensed operator, then intercept the decoded video at the device output using HDCP strippers or equivalent HDMI interception. The raw signal is re-encoded and restreamed into their unauthorized front ends. While common in broader piracy, management’s references to “advanced technology” imply vectors 1–2 are the primary concern.
These attacks are categorically different from consumer “stream-jacking” on open platforms (e.g., social engineering or account takeovers). They target the encrypted, B2B-protected core of Evolution’s service such as privileged keys, distribution infrastructure, and high-fidelity source streams, making them more akin to supply-chain breaches than simple content theft.
Geographical hotspots and the Philippine link
Management has been explicit that these attacks are geographically concentrated in Asia. Although specific countries are not officially named, the operational context of the iGaming industry points toward major grey and unregulated markets in Southeast and East Asia, which have historically been significant contributors to Evolution's growth.
An interesting piece of analysis from the advisory firm Regulus Partners provides a strong hypothesis for the identity and motivation of the attackers. The report highlights that the emergence of these sophisticated cyberattacks in Q3 2024 coincides with the shutdown of the Philippine Offshore Gaming Operators (POGO) sector. The POGO industry was known to have deep connections to organized crime, with many operators implicated in serious offenses such as mass people trafficking and money laundering.
The regulatory crackdown in the Philippines displaced numerous well-funded and technologically capable criminal organizations. These groups, having lost a primary revenue stream, had a clear motive to find a new one. By targeting Evolution they could leverage their existing technical expertise to hijack a premium product and continue their illicit gambling operations.
This attribution is critical as it suggests that Evolution is not fighting opportunistic hackers, but rather a coordinated campaign by a sophisticated criminal enterprise. This transforms the problem from a simple technical issue into a prolonged, but manageable, strategic challenge against a determined adversary.
Quantifying the headwind with management commentary
Review of management statements
(Q3 2024 - Q2 2025)
The evolution of management's public commentary provides a clear narrative of the company's journey in confronting this crisis, from initial disclosure to the implementation of a comprehensive and successful response.
Q3 2024, the disclosure: The issue was first brought to the attention of investors during the Q3 2024 earnings call. CEO Martin Carlesund was direct, stating, "we have also seen an increase in amounts of cyberattacks against our Asian video distribution... Cyber criminals use advanced technology to intercept our video feed, manipulate it and redistribute it without authorization which leads to loss of revenue... it has negatively impacted the third quarter.". The key takeaways from this initial statement were the acknowledgment of a direct negative revenue impact and the characterization of the threat as technologically "advanced" and having "significantly increased" in activity.
Q4 2024, managing expectations: By the end of the year, it was clear the problem was not a fleeting one. In the Q4 2024 call, Carlesund confirmed the ongoing impact: "we are still hampered by the cyber-attacks and fraud in the Asian region... growth is clearly affected in the quarter.". Crucially, he began to manage investor expectations for a protracted resolution, reminding them, "I said already in Q3 that we expected it would take a couple of quarters to come to terms with the situation and we are in that process right now.". This statement was a clear signal that there would be no immediate solution and that the financial impact would likely persist into 2025.
Q1 2025, the pain of the cure: The first quarter of 2025 saw a narrative shift towards explaining the impact of the company's own countermeasures. Carlesund explained, "The second activity with an impact of the result is the continued work to stop the criminal cyber activity that we face in Asia. We are making constant progress, but the measures do impact the network in general and the revenue is in line with what we have seen in the last couple of quarters.". This was a critical admission that the actions being taken to secure the network were themselves a source of revenue headwind, as they involved shutting down compromised traffic and partners. The result was a third consecutive quarter of flat revenue in the region.
Q2 2025, a glimmer of optimism: After a full year of battling the issue, the Q2 2025 report marked a potential turning point. While still acknowledging the "ongoing issues with cybercrime and video stream hijacking in Asia," Carlesund's commentary in the interim report noted that "new measures are being deployed and the region is seeing a return to growth, with cautious optimism for the rest of 2025." A summary of the earnings call captured this sentiment, highlighting
"Growth in Asian markets supported by... cutting-edge technical measures against cybercrime.". This was the first indication to the market that the company's strategy was beginning to yield positive net results.
Financial impact assessment
While management has consistently stated that it is "very hard to quantify the Asian growth" impact precisely, the effect is clearly visible in the company's reported regional financial data.
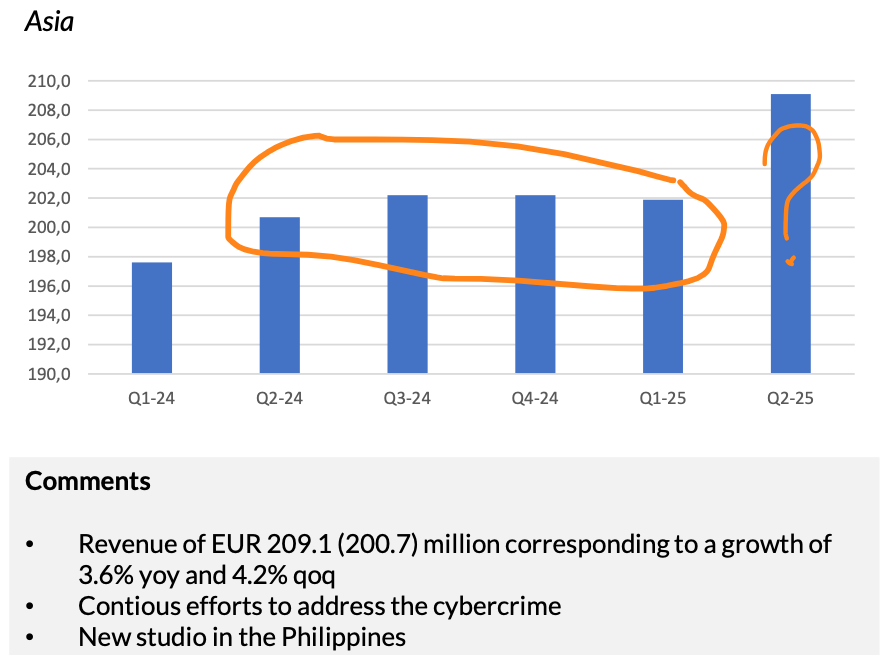
Direct revenue impact: The most significant consequence has been the dramatic deceleration and subsequent stagnation of revenue from the Asian market. Prior to the attacks, the region consistently posted strong double-digit growth. The attacks halted this momentum entirely. The following table tracks management's evolving narrative against the hard financial data, illustrating the correlation between the stated severity of the problem and the reported results.
Indirect margin impact: The fight against cybercrime has had a tangible effect on group-level profitability. The costs associated with developing and deploying countermeasures, combined with the drag from the high-margin Asian segment's stalled growth, have compressed the company's industry-leading EBITDA margins. In the Q1 2025 earnings call, Carlesund explicitly linked the quarter's 65.6% EBITDA margin, which was below the company's full-year guidance range of 66% to 68%, to the "cyberattack countermeasures in Asia". While the company maintained its full-year guidance, this demonstrated that the problem was significant enough to affect the entire group's financial performance.
The financial data reveals the cost of Evolution's response. The revenue plateau observed through Q4 2024 and Q1 2025 was not solely a result of lost revenue to criminals. It was also a direct consequence of Evolution's deliberate tactical decision to "shut down" compromised parts of its network and remove offending customers. This willingness to absorb a self-inflicted revenue hit to secure the network's long-term integrity is a positive signal of management's strategic focus. The data now supports a view of containment and gradual recovery, not chronic deterioration.
Assessment of Evolution's countermeasures
A two-folded defense strategy
Evolution has implemented a comprehensive, two-folded strategy to combat the stream hijacking, combining sophisticated technical solutions with strong commercial actions. This approach targets both the method of attack and the illicit ecosystem that profits from it.
Technical countermeasures: While management has prudently avoided disclosing precise technical details, their references to "new technical measures" and "cutting-edge technical measures" point to the deployment of industry-standard and proprietary anti-piracy solutions. These capabilities likely include:
Forensic watermarking: This technology embeds a unique digital watermark into each individual video stream delivered to an operator. If a hijacked stream is discovered, this watermark can be extracted and analyzed to pinpoint the source of the leak. This is a critical tool for attribution and enforcement.
Enhanced encryption and DRM: Strengthening the cryptographic protocols that protect the video stream in transit. This involves using the latest versions of security protocols (SRTP and DTLS), making it more difficult for attackers to break the encryption or bypass the DRM checks that control access to the content.
Proactive network monitoring: Intrusion detection and traffic analytics flag anomalies in real time (e.g., unusual stream origination or geolocation), enabling rapid intervention and, as noted by Carlesund, improved theft detection.
Commercial countermeasures: Technology alone is insufficient. Evolution leverages contracts and partner relationships “both technically and commercially” to force remediation. Once watermarking or telemetry traces a leak to an operator, Evolution enforces terms: terminate abusive end-users, upgrade security, or remove non-compliant operators. This “solidifying our protection” approach actively clears bad actors, even at the expense of near-term revenue.
Is the defense strategy effective?
The effectiveness of this dual strategy can be measured by its impact on the Asian segment's financial trajectory. The evidence shows this is a winnable battle.
Successful containment: The primary achievement of the countermeasures was arresting a potential revenue collapse. Instead of declining, Asian revenue stabilized and remained flat for three consecutive quarters following the initial disclosure. This plateau demonstrates that the company's defensive actions were successful in containing the problem and preventing it from spiraling out of control, which lower revenue would have signalled.
First recovery: The Q2 2025 financial results provide the first concrete evidence that the strategy is enabling a recovery. The reported revenue of €209.1 million represented the first meaningful sequential and year-over-year growth (4.2%) since the crisis began. This suggests that the positive impact of legitimate network growth is now beginning to overpower the negative impact of shutting down compromised traffic.
This situation, however, reveals an important dependency in Evolution's business model, particularly in unregulated markets. The company's security is linked to the security and compliance of its hundreds of downstream operator clients. A single operator with lax security can become a vector of attack that affects the entire network. This reality may compel Evolution to adopt a more stringent partner selection process in the future, prioritizing security and compliance over sheer market reach, which could in turn moderate the pace of its expansion in these higher-risk regions.
Long-term implications
A manageable risk, not an unsolvable challenge
While Evolution's countermeasures have proven effective at managing the acute phase of the stream hijacking crisis, the underlying problem is best viewed by investors as a manageable, structural risk inherent to its Asian operations, rather than a temporary technical challenge. Several factors support this assessment.
The nature of the adversary: The strong evidence linking the attacks to organized criminal groups displaced by the POGO shutdown is the most critical factor. Unlike opportunistic hackers who might move on to softer targets, these are sophisticated, profit-motivated enterprises. This establishes a high likelihood of a persistent "cat-and-mouse" game, where Evolution must continuously invest in escalating levels of security to defend against an adversary that is constantly evolving its attack methods.
The permissive operating environment: The attacks are concentrated in Asia's grey and black markets, which are characterized by a lack of robust regulatory oversight and legal enforcement mechanisms. This makes it exceedingly difficult, if not impossible, for Evolution to pursue effective legal action against the perpetrators. The risk is therefore inherent to the nature of the markets themselves.
The increased "cost of doing business": The fight against this threat is not a one-time expense. The need for continuous investment in advanced security technologies, heightened network monitoring, and a more rigorous commercial compliance function represents a permanent increase in the operational expenditure required to do business in these markets.
Impact on Asian growth outlook
This new reality of a persistent, high-level security threat fundamentally recalibrates the long-term investment thesis for Evolution's Asian segment. The period of "easy Asian growth with few questions asked and no local response" is definitively over.
Slower, cleaner growth: Unregulated-market growth will proceed more deliberately and with higher upfront cost. Deeper partner due diligence and pruning of non-compliant operators reduce leakage but act as a natural brake. The assumption of frictionless, hyper-growth must be replaced with a model that accounts for "slower but cleaner" growth with lower leakage risk.
Strategic move to regulated markets: The shift accelerates expansion into licensed jurisdictions. The company's significant investment in launching a new, state-of-the-art studio in the Philippines in June 2025 is the most tangible evidence of this strategic pivot. By establishing a major operational hub within the first licensed iGaming jurisdiction in Asia, Evolution is proactively de-risking its regional footprint, albeit in a market that may grow more slower and methodically than the grey markets of the past.
Recalibrating profit margins: Expect higher ongoing operational expenses (% of Asia revenue), selective capex for hardened infrastructure, and more rigorous vendor/operator standards, but to some extent offset by lower fraud/leakage and steadier cash conversion.
What’s the outlook?
Evolution AB’s Asian operations have faced a sophisticated, organized-crime-led video stream hijacking campaign that targets the core of its delivery. The disruption has been material. What had been rapid regional growth stalled for roughly a year, with knock-on pressure on group EBITDA margins. Management’s response has been a coordinated mix of technical countermeasures, partner vetting, and operational hardening, which has contained the threat and set the stage for a measured recovery, underscoring strong execution and strategic discipline.
Given the adversary’s capabilities and the permissive regulatory environments in parts of Asia, the threat should be treated as a permanent, structural cost of doing business. It remains economically rational to keep fighting, but with a slightly different strategy. Evolution is pivoting toward regulated markets where protections and enforcement are stronger. The new studio in the Philippines exemplifies this shift, implying slower but higher-quality growth that is more capital-intensive upfront yet more secure and sustainable over time, providing a sturdier long-term operating base.
For investors, the core thesis holds. Evolution’s moat is driven by product breadth, studio scale, distribution, and it remains intact. Global demand for online casino content continues to expand and management has shown it can navigate crises decisively.
Expectations for Asia should be recalibrated toward steadier, regulated growth, with the Philippines serving as a key proof point for the strategy. Net-net, a disruptive challenge has been converted into a catalyst for change and stronger operations.
The stock outlook for me is still that of a compelling compounder, with the Asian trajectory shifting from hyper-growth to durable, regulated expansion.




Don’t you think if it’s going to be expensive for Evolution than it will be expensive for the cyber attackers to keep funding. Eventually they will have to thwart their efforts because the roi is not worth it.
u keep stealing my post ideas! although i would probably never go as deep as you, good work!